ARTEMIS: Autonomous AI Red Teaming Explained

Written by Rafter Team
January 28, 2026

Most application security tools answer a narrow question: “Does this code match a known bad pattern?” Real attackers don’t think that way—they chain weak assumptions, misconfigurations, and logic gaps into exploits. ARTEMIS is built to do the same, but safely and continuously.
ARTEMIS is an autonomous red-teaming agent. It plans attacks, adapts to feedback, and treats vulnerabilities as behaviors—not isolated lines of code.
Why ARTEMIS matters now
Scanners are fast and deterministic, but shallow. Manual red teams are deep, but slow and expensive. ARTEMIS sits in a new category: autonomous AI red teaming that runs often, learns, and keeps pressure on real systems.
In this post, you’ll see:
- What ARTEMIS actually is (and what it isn’t)
- How agentic testing differs from static analysis and fuzzing
- The loop that lets ARTEMIS learn like an attacker
- Where it slots into a modern AppSec program
What ARTEMIS is (and is not)
ARTEMIS is not a one-shot scanner or a single model. It’s an agent that probes software the way a human attacker would—form a hypothesis, act, observe, and adapt.
From tools to agents
Traditional tools:
- Take inputs → apply rules → emit findings
ARTEMIS:
- Observes a system
- Forms exploit hypotheses
- Chooses and executes tools to test them
- Evaluates outcomes and decides what to try next
Instead of asking “Is this line risky?”, it asks “How could I break this system?”
What it’s designed to uncover
- Multi-step authentication bypasses
- Privilege escalation chains
- Cross-component logic bugs
- Vulnerabilities that emerge after state changes
Think behaviors, not signatures. ARTEMIS treats vulnerabilities as sequences of actions and decisions—exactly how real exploits unfold.
How ARTEMIS works
The agent runs a tight loop that mirrors human offensive workflows:
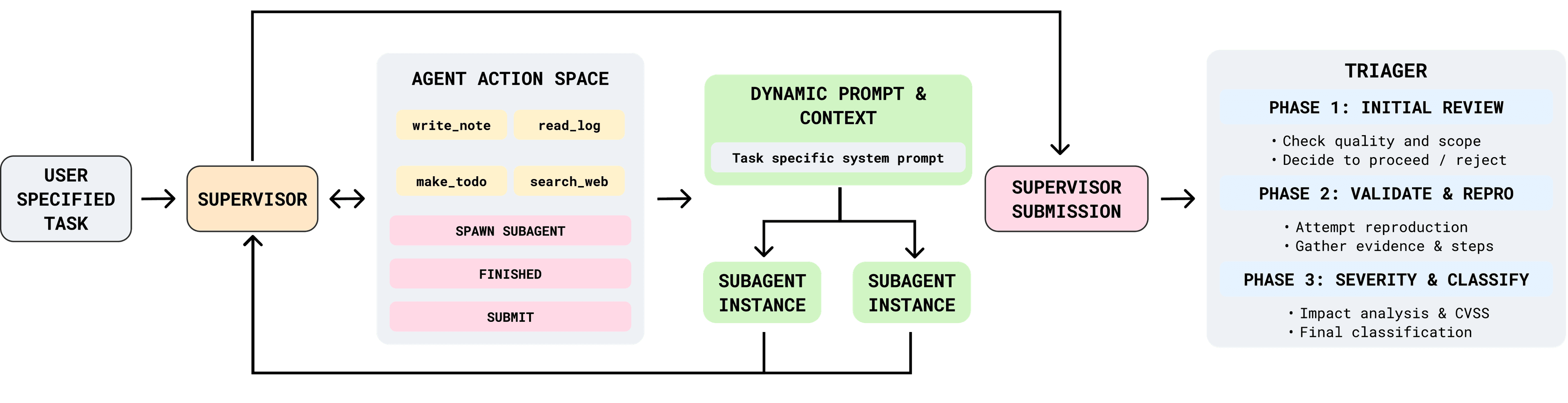
Each pass tightens the agent’s understanding of the system and the likelihood of a real exploit.
Guardrails and orchestration
ARTEMIS runs inside controlled environments with explicit action limits and clear separation between observation and mutation. That makes the work auditable—and safe enough to run continuously in production-like contexts.
Tool use as a first-class move
The agent doesn’t assume it knows everything. It decides which tool to use at each step:
- Static analyzers for code hotspots
- Probing scripts for surface mapping
- Targeted tests to validate exploit chains
- Custom checks when the system shows unusual behavior
The value isn’t in “AI magic.” It’s in orchestrating familiar offensive tools with attacker-style planning and memory.
Why this is different from scanners, fuzzers, and humans
- Static analysis excels at known patterns and regressions, but it’s local.
- Fuzzing is great for input-driven crashes but rarely builds attack narratives.
- Human red teams are creative and systemic, but scarce and episodic.
ARTEMIS is closest to a human red team—automated and tireless. It plans attacks, remembers what worked, and keeps iterating until the window closes.
What teams get out of ARTEMIS
Continuous pressure without the price tag
Traditional red teaming is expensive and infrequent. ARTEMIS delivers:
- On-demand testing in real environments
- Continuous probing instead of quarterly snapshots
- Scalable depth across services and deployments
Coverage for the messy middle
Scanners catch known classes. Humans catch novel chains. ARTEMIS covers the gap where real incidents live by:
- Connecting weak signals across components
- Surfacing plausible attack paths, not just alerts
- Demonstrating behavior that looks like real exploitation
Fit in a layered pipeline
- Scanners for baseline coverage
- Reasoning models for explanation and triage
- Autonomous agents for attack simulation (ARTEMIS)
It’s a depth amplifier, not a replacement.
What ARTEMIS doesn’t replace
- Human judgment about risk, business context, and ethics
- Deterministic tools for compliance and regressions
- The need for clear guardrails and review in production
Treat it as a powerful assistant that raises the floor and keeps pressure on systems—not an oracle you blindly trust.
Takeaway
ARTEMIS marks a shift from static checks to adaptive, attacker-style behavior. It connects actions into narratives, learns from feedback, and exposes the vulnerabilities that actually get exploited. Teams that think like this won’t just scan faster—they’ll defend smarter.